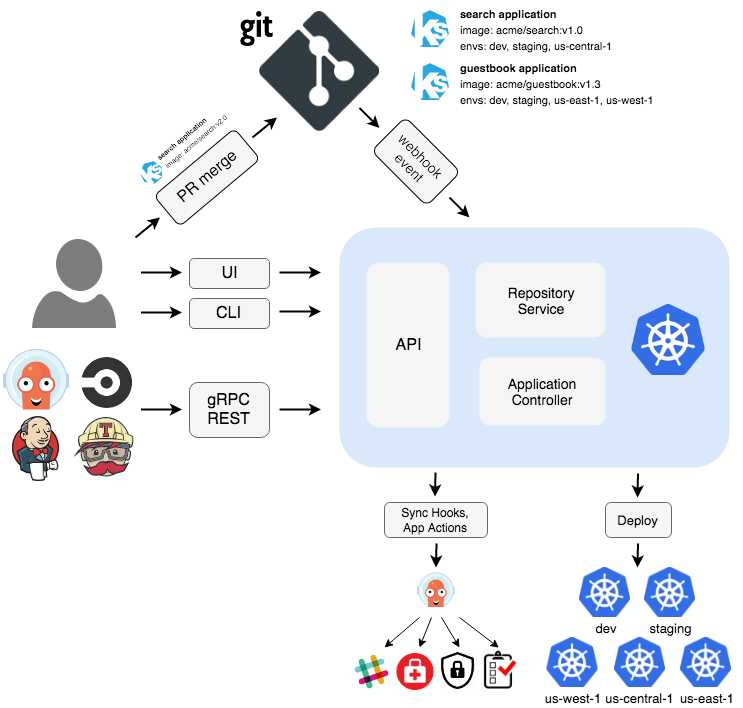
Architecture
https://argo-cd.readthedocs.io/en/stable/operator-manual/architecture/
Argo setup
클러스터에 접근 가능한 곳에 argocd를 설치한다 (bastion server)
Argo CD 설치
- services
- application resources
[ec2-user@ip-172-31-65-113 .kube]$ kubectl create namespace argocd
namespace/argocd created
[ec2-user@ip-172-31-65-113 .kube]$ kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
customresourcedefinition.apiextensions.k8s.io/applications.argoproj.io created
customresourcedefinition.apiextensions.k8s.io/applicationsets.argoproj.io created
customresourcedefinition.apiextensions.k8s.io/appprojects.argoproj.io created
serviceaccount/argocd-application-controller created
serviceaccount/argocd-applicationset-controller created
serviceaccount/argocd-dex-server created
serviceaccount/argocd-notifications-controller created
serviceaccount/argocd-redis created
serviceaccount/argocd-repo-server created
serviceaccount/argocd-server created
role.rbac.authorization.k8s.io/argocd-application-controller created
role.rbac.authorization.k8s.io/argocd-applicationset-controller created
role.rbac.authorization.k8s.io/argocd-dex-server created
role.rbac.authorization.k8s.io/argocd-notifications-controller created
role.rbac.authorization.k8s.io/argocd-server created
clusterrole.rbac.authorization.k8s.io/argocd-application-controller created
clusterrole.rbac.authorization.k8s.io/argocd-applicationset-controller created
clusterrole.rbac.authorization.k8s.io/argocd-server created
rolebinding.rbac.authorization.k8s.io/argocd-application-controller created
rolebinding.rbac.authorization.k8s.io/argocd-applicationset-controller created
rolebinding.rbac.authorization.k8s.io/argocd-dex-server created
rolebinding.rbac.authorization.k8s.io/argocd-notifications-controller created
rolebinding.rbac.authorization.k8s.io/argocd-server created
clusterrolebinding.rbac.authorization.k8s.io/argocd-application-controller created
clusterrolebinding.rbac.authorization.k8s.io/argocd-applicationset-controller created
clusterrolebinding.rbac.authorization.k8s.io/argocd-server created
configmap/argocd-cm created
configmap/argocd-cmd-params-cm created
configmap/argocd-gpg-keys-cm created
configmap/argocd-notifications-cm created
configmap/argocd-rbac-cm created
configmap/argocd-ssh-known-hosts-cm created
configmap/argocd-tls-certs-cm created
secret/argocd-notifications-secret created
secret/argocd-secret created
service/argocd-applicationset-controller created
service/argocd-dex-server created
service/argocd-metrics created
service/argocd-notifications-controller-metrics created
service/argocd-redis created
service/argocd-repo-server created
service/argocd-server created
service/argocd-server-metrics created
deployment.apps/argocd-applicationset-controller created
deployment.apps/argocd-dex-server created
deployment.apps/argocd-notifications-controller created
deployment.apps/argocd-redis created
deployment.apps/argocd-repo-server created
deployment.apps/argocd-server created
statefulset.apps/argocd-application-controller created
networkpolicy.networking.k8s.io/argocd-application-controller-network-policy created
networkpolicy.networking.k8s.io/argocd-applicationset-controller-network-policy created
networkpolicy.networking.k8s.io/argocd-dex-server-network-policy created
networkpolicy.networking.k8s.io/argocd-notifications-controller-network-policy created
networkpolicy.networking.k8s.io/argocd-redis-network-policy created
networkpolicy.networking.k8s.io/argocd-repo-server-network-policy created
networkpolicy.networking.k8s.io/argocd-server-network-policy createdArgo CD CLI 설치
bastion server - linux 설치
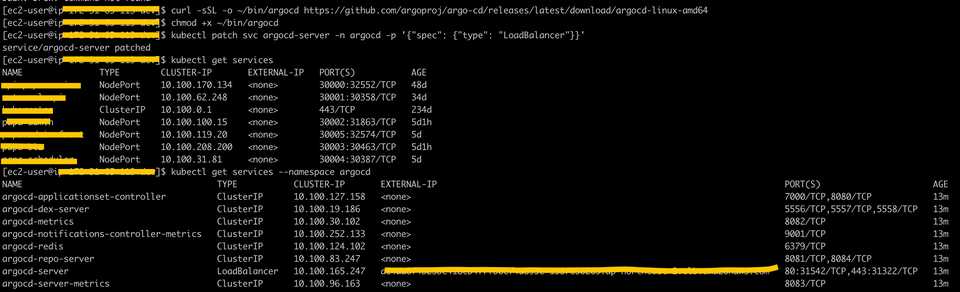
[ec2-user@ip-172-31-65-113 dev]$ curl -sSL -o ~/bin/argocd https://github.com/argoproj/argo-cd/releases/latest/download/argocd-linux-amd64
[ec2-user@ip-172-31-65-113 dev]$ chmod +x ~/bin/argocdArgo CD API Server 노출
External IP 에서 접근 허용
[ec2-user@ip-172-31-65-113 dev]$ kubectl patch svc argocd-server -n argocd -p '{"spec": {"type": "LoadBalancer"}}'
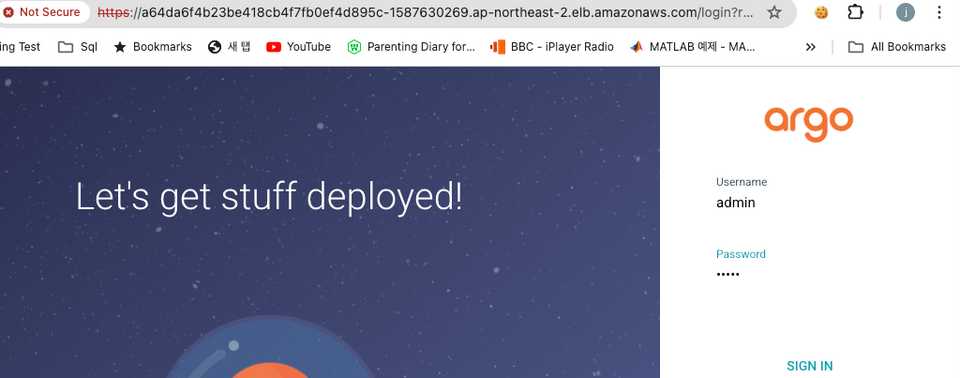
service/argocd-server patched- external IP address: a64da6f4b23be418cb4f7fb0ef4d895c-1587630269.ap-northeast-2.elb.amazonaws.com
Login CLI
- id: admin
-
pw: nzJVTCDXvD0447rj
[ec2-user@ip-172-31-65-113 dev]$ argocd admin initial-password -n argocd nzJVTCDXvD0447rj
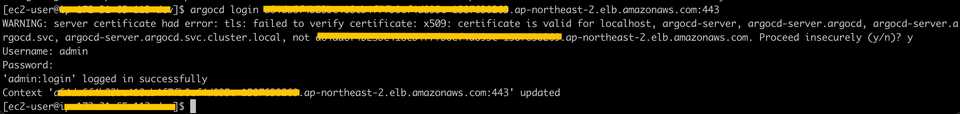
CLI LOGIN
argocd login a64da6f4b23be418cb4f7fb0ef4d895c-1587630269.ap-northeast-2.elb.amazonaws.com:443Register Cluster
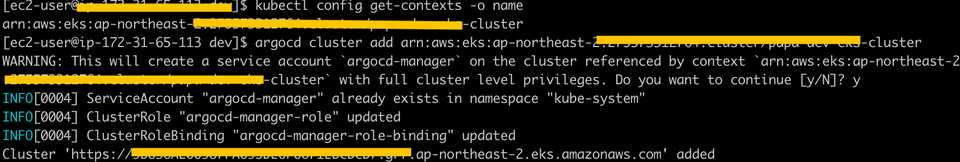
- 클러스터에 연결이 안된 이슈가 있어서 직접 클러스터를 선택해서 연결해줌
# 클러스터 조회
kubectl config get-contexts -o name
# 클러스터 연결
argocd cluster add arn:aws:eks:ap-northeast-2:275573312764:cluster/papa-dev-eks-clusternamespace 선택
kubectl config set-context --current --namespace=argocd
kubectl config set-context --current --namespace=defaultBitbucket helm repository 연결
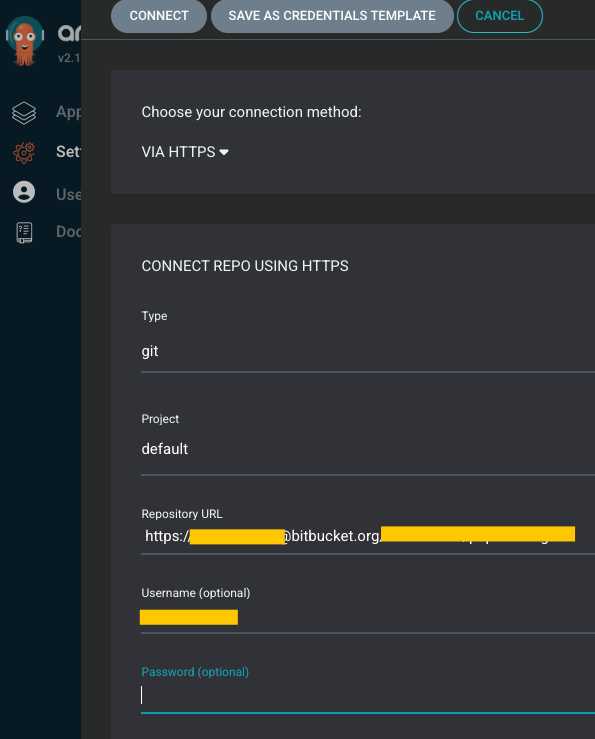
- argocd ip login
-
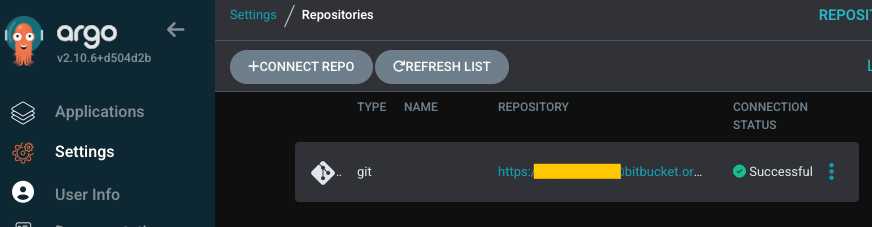
Settings > Repository > Connect Repo
-
project 생성
Application 생성
- Project Name: 위에서 생성한 Project 이름 선택 (default)
-
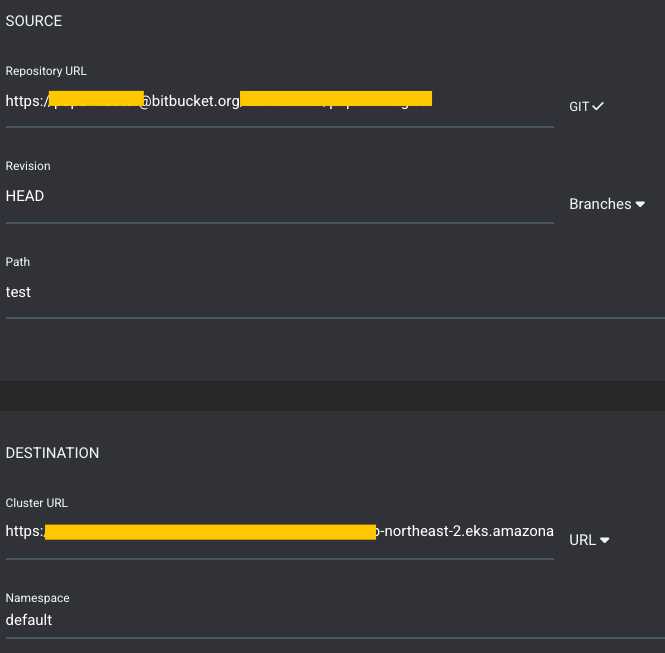
SOURCE: 위에서 생성한 REPO 선택
- Path: Chart.yaml 있는 디렉토리 이름
-
DESTINATION: 위에서 생성한 Cluster Server 선택
-
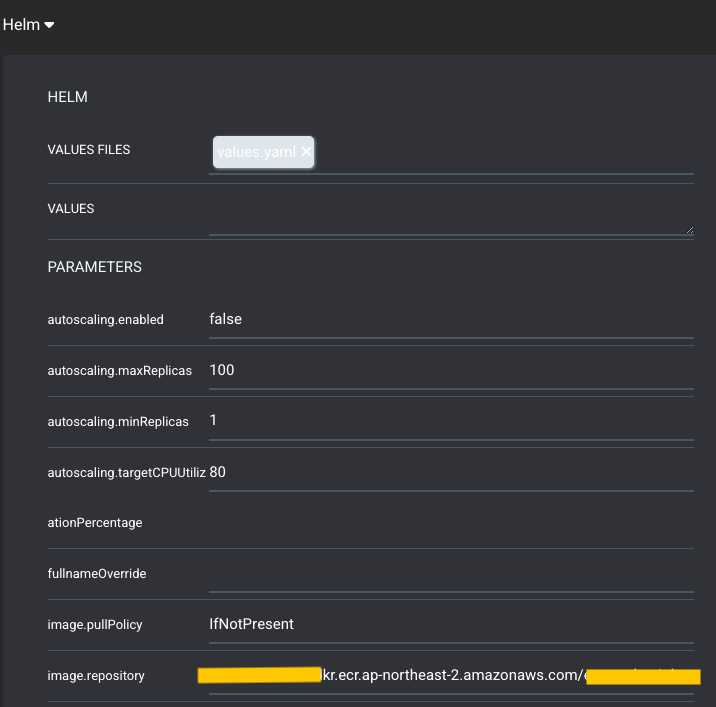
repo 가 헬름으로 확인되면 Helm 챕터가 나오고 values.yaml 을 선택 할 수 있다
- 후에 env 에 맞는 vaules.yaml 선택 (values-dev.yaml, values-live.yaml)
Trouble shooting
Unable to create application: application spec for test is invalid: InvalidSpecError: application destination server ’https://9B836AE00987FA095DE6F6671EBCDCD7.gr7.ap-northeast-2.eks.amazonaws.com’ and namespace ‘argocd’ do not match any of the allowed destinations in project ‘default’
Project 설정을 cluster 서버를 찾아서 연결해줌
Reference
https://www.sktenterprise.com/bizInsight/blogDetail/dev/2606
https://www.eksworkshop.com/docs/automation/gitops/argocd/cluster_bootstrap
https://argo-cd.readthedocs.io/en/stable/getting_started/
https://argo-cd.readthedocs.io/en/stable/cli_installation/#installation